
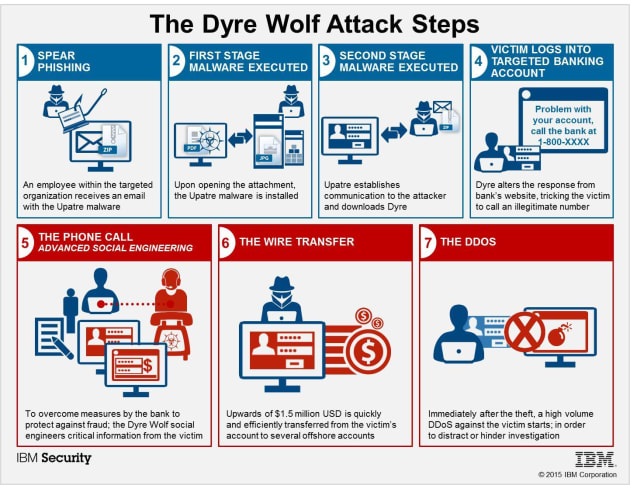
Hackers continue their brazen attacks on organizations and
are even having their victims call them on the phone to hustle them out
of their company's money. That's what IBM's Security Intelligence
division has discovered while researching a malware-based attack they
have dubbed The Dyre Wolf that's responsible for stealing more than $1
million. The coordinated campaign uses targeted spear phishing emails,
malware and good ol' chatting-on-the-phone social engineering to go
after organizations that use wire transfers.
According to IBM threat researchers, the attack starts
with a single user opening an infected email attachment. Once opened,
that malware contacts the attacker's server then downloads and installs
the Dyre malware which hijacks the user's address book and mails itself
throughout the organization.
Then things get real fun. When a victim with an infected
computer attempts to log in to a banking site monitored by the malware,
it throws up a new screen that says that the site is experiencing issues
and presents a phone number for that person to call to make their
transaction. Once the attackers have all the information, a wire
transfer is made that runs through a series of international banks to
thwart authorities.
The entire attack relies on social engineering. The
victims have to open the initial attachment and make the phone call that
could cost their company a lot of money. This circumvents passwords and
two-factor authentication because it goes around the digital entrance
and gets critical information directly from the victim. IBM recommends
companies train their employees to never open or click suspicious
attachments or links and to remind employees that banks will never ask
them for their banking credentials.
0 comments :
Post a Comment